Well, its been a while since I’ve updated, well this is something to fill up the blank posts… hahaha…
Normally when you managed to get into someone’s network, be it protected with WPA/WPA2 or WEP, (you can read my post on hacking WEP & WPA networks) once you’ve gained the access, it would be much more fun to actually see their traffic.. One thing led to another, that’s why securing your networks is crucial. It has now become very sophisticated that you can even control a network by just using your phone. In this case, I’ll be using the latest Google Nexus 4 by LG. I’ve rooted the phone the first day I get my hands on it.. hahahha
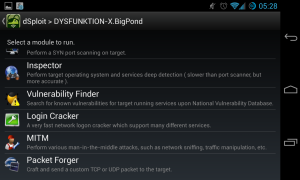
So basically I’ve connected to my home wifi, DysfunktionTech, and start the dSploit app. I’ve selected my laptop as the victim, DYSFUNKTION-X.
Here, you can scan for opened ports. With the result, you can start vulnerability finder to check whether it is vulnerable or not. MITM is a very powerful attack to the defenseless clients in the network. This type of attack, MITM (Man-in-the-middle) is pretending to be the gateway to the clients by spoofing the ARP requests.
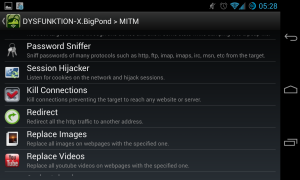
These are the common actions that can be done using MITM attack. What is does is basically changing the network packet sent to the client. You can hijack a browsing session, get password for ftp / pop3 traffic, kill any connection to the victim, redirect webpages and even replace images or videos to be presented to the victim pc.
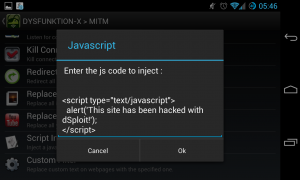
Here’s an example, you can inject a javascript to every pages that the victim opens. This is a very simple packet manipulation. The possibilities are limitless.
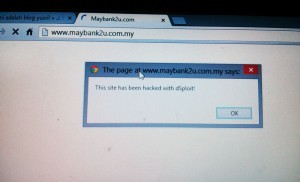
and here is the result at the victim PC.
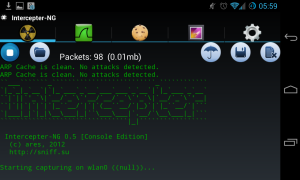
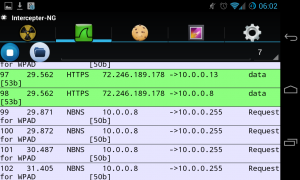
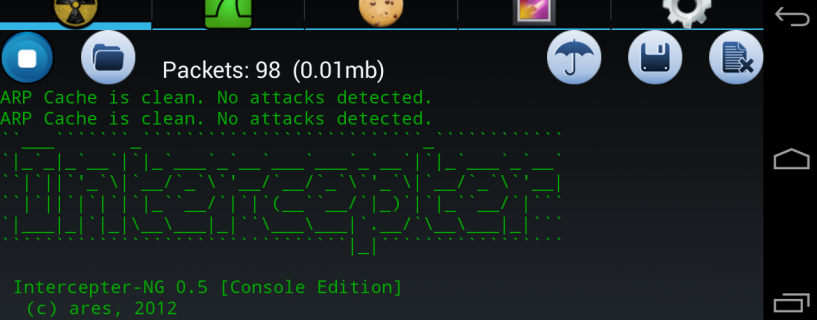
You can also use Intercepter-NG to capture the packets.
ref:
dSploit – The most complete and advanced IT security professional toolkit on Android.
Intercepter-ng
Google Play (Intercepter-NG)

 by yusri
by yusri